With Garmin back up online many people probably don’t care how Garmin resolved WastedLocker ransomware attack that was carried out on their systems last week.
However, BleepingComputer has received some key information about how Garmin got back online, and it could place Garmin in an awkward situation.
BleepingComputer was the first company to confirm Garmin was not doing maintenance on their systems but in fact, had suffered a major security breach having many systems encrypted by the WastedLocker ransomware disabling all access to the systems it affected. They acquired this information from employees who shared photos of encrypted workstations, and it looks like the latest bit of news is via similar sources.
Garmin received a WastedLocker decryption key
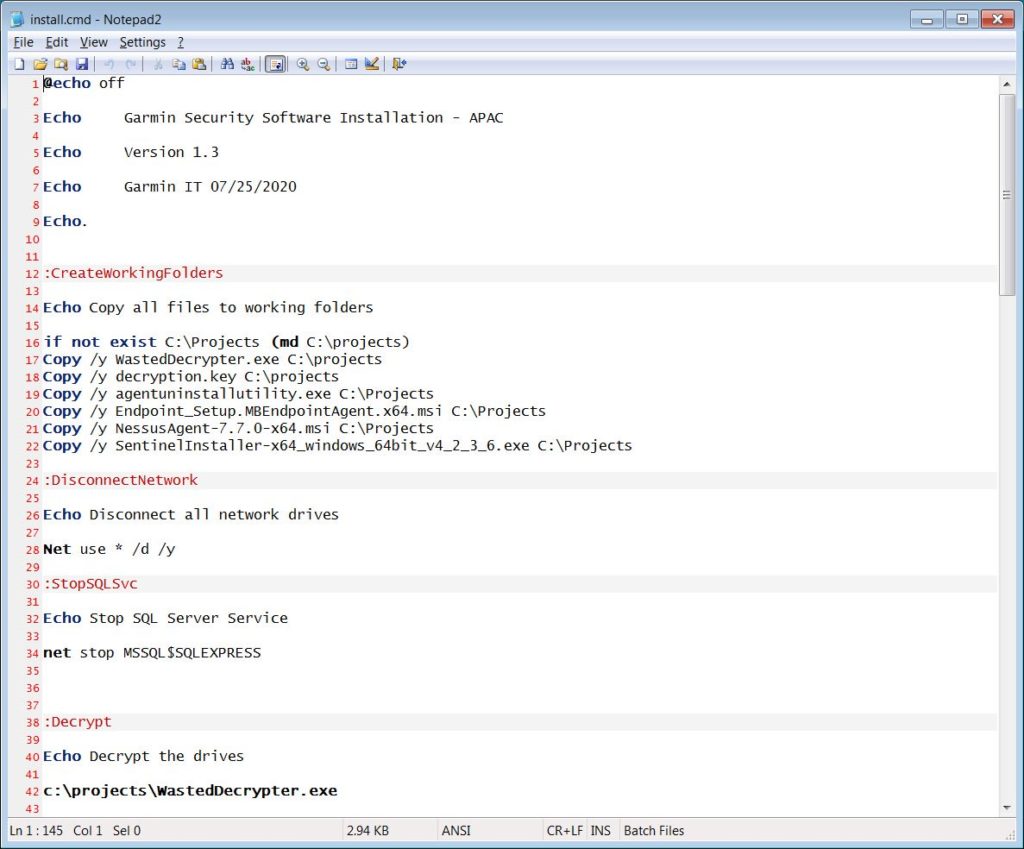
BleepingComputer has now gained access to an executable created by the Garmin IT department to decrypt a workstation and then install a variety of security software on the machine.
It confirms the attack was the WastedLocker ransomware, and this is a particularly effective piece of software, in that it is effectively impossible to create a decryptor without being supplied the decryption key direct from the perpetrator.
This would imply that Garmin has almost certainly paid the ransom, which was likely the $10 million originally asked for.
When the executable form the Garmin IT department is extracted some of the scripts that are run contain timestamps of 07/25/2020, this would make it likely that Garmin paid up within 48 hours of the attack being carried out.
Garmin decryptor script does not do a clean install
Decryptor in Garmin’s WastedLocker Ransomware attack from BleepingComputer.com on Vimeo.
BleepingComputer advises that after any ransomware, you should wipe and install everything with a clean image to avoid introducing new weaknesses that may have been introduced as part of the attack. The script Garmin has issued does not do this, but we don’t know if this will then be done at a later date.
The decryptor enclosed in the package includes references to both cybersecurity firm Emsisoft and ransomware negotiation service firm Coveware. Neither company were will to make a comment.
Evil Corp & US Sanctions
One of the biggest concerns for Garmin could be how the US government feel about this situation. WastedLocker is attributed to Evil Corp, who is on the US sanctions list. In theory, this could mean that Garmin could face serious financial fines from the US government for trading with Evil Corp. Of course, this would mean someone would have to prove Garmin actually transferred money to them, and the US may have better things to deal with at the moment.
What now?
Garmin is still recovering from the attack, most of their systems are online, but many are still limited.
They say no data has been lost, and this is likely true as they paid the ransom.
Currently, Garmin has not been very forthcoming about the whole problem, communication during the outage was poor at best, and since then they have only provided a brief response stating they were a victim of a cyberattack that encrypted some of our systems on July 23, 2020.
One concerning issue is they claim that no personal data is stolen, they didn’t appear to comply with the rules established by the GDPR stating that you need to inform customers at the earliest opportunity. They have also no advised that users update their passwords.
To reiterate – With no official word from Garmin, all of the above is speculation in regards to what Garmin did and did not do to get the decryption key. However, the information from BleepingComputer paints a very specific picture.
As WastedLocker is attributed to Evil Corp, who has been sanctioned by the US govt, this can become quite a sticky situation for Garmin.https://t.co/ujYD4Qixqs
— BleepingComputer (@BleepinComputer) August 1, 2020